We discussed how a centralized server should authenticate our requests rather than every service. Building a service that authenticates and authorizes is difficult, and doing so across multiple services makes it even more difficult.
A tried-and-true protocol exists to accomplish even the most challenging software tasks. OpenID is one of these protocols that is widely used and works well in many different situations.
In this blog post, we will build our own authentication server and see how it works.
OpenID
OpenID is an identity protocol that lets a user prove who they are. You may have noticed that authentication is happening everywhere. Even in the medium, you can verify yourself with Google, Facebook, etc.
Most people confuse OAuth and OpenID. OAuth is a authorization protocol and OpenID is a authentication Protocol
OpenID can be used to do authentication for multiple device types with UI and non-UI. So to satisfy the need OpenID divides the clients into two types
- Confidential Clients — Client’s which can be trusted like Webserver, API and Smart TV
- Public clients — This strategy is used for SPA-based clients; according to the most recent best practices, it is preferable to utilize the BFF pattern to prevent disclosing secrets.
Again, different flows can be supported, but this article will only talk about the authorization code flow and PKCE. This is a common flow utilized by all applications.
Authorization Code Flow
Image Courtesy : Auth0 — https://auth0.com/docs/get-started/authentication-and-authorization-flow/authorization-code-flow
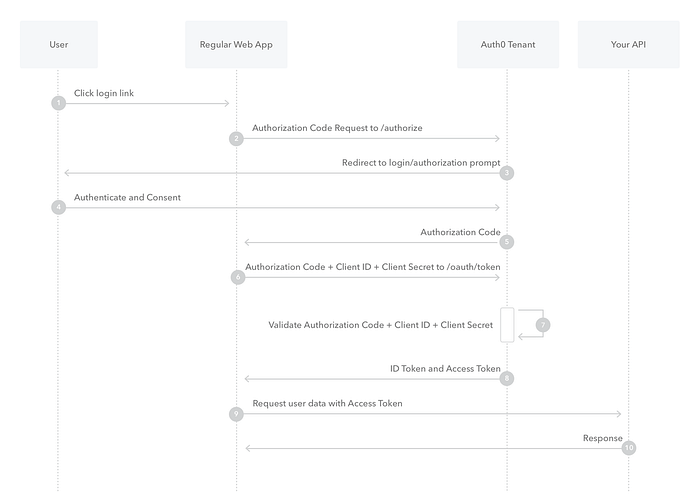
Even the name says the Authorization code flow we will concentrate only on the first few steps
- User clicks Login Link and Get redirected to the Authorization server
- Authorization server authenticates the User and ask for consent
- Once the authentication is successful we can get a Identity Token
In this part, we will create an identity server, and in the next part, let's talk about how to connect the client (webapp) together.
Setting up Identity Server
Creating an OIDC server manually is possible, but using a framework simplifies the process. Dundee.IdentityServer is a framework for DotNet, and most of the market leaders use it.
The first thing to do is install the template at the global level
dotnet new --install Duende.IdentityServer.TemplatesNext, let's add a simple solution and use the template to create a project. I am trying to keep everything in the command line, but obviously all the steps can be done in Visual Studio too.
mkdir secure
cd secureLets create a solution and start adding the project for the Identity server from the Templates which we added.
dotnet new sln -n authenticationserver
mkdir src
cd src
dotnet new isempty -n identityserverIs Empty template adds the default Webapi project and configures the identity server so that all the OpenID protocol APIs can be used. There are different kinds of OpenId endpoints that are used for different things.
As a developer, all we have to do is set up the data that the API will send, and that’s it. In our first step, we need to give a client. In our web app, authentication will be done by redirecting to us. The configuration can be used to register the client.
We’re adding the client that uses Code as the grant type and gets the scope of OpenID (user ID) and Profile (Profile information). These are the user’s standard scopes.
This should be good for us now, and we can check the discovery document from the same place. You can use to get the discovery API.
https://localhost:<<Port>>/.well-known/openid-configuration
This document provides the Scope that the server support and different methods of the grant types.

From the screen shot above, you can see scopes and grant types displayed. In the next blog post, we will include some UI and some test users.
Next Blog Post : https://satish1v.medium.com/building-authentication-server-ui-dda25510da6d
